Uncategorized
What are address poisoning attacks in crypto and how to avoid them?
Address poisoning attacks involve tracking, misusing or compromising cryptocurrency addresses.
Address poisoning attacks are malicious…

Address poisoning attacks involve tracking, misusing or compromising cryptocurrency addresses.
Address poisoning attacks are malicious tactics used by attackers who can reroute traffic, interrupt services, or obtain unauthorized access to sensitive data by inserting bogus data or changing routing tables. The integrity of data and network security are seriously threatened by these assaults, which take advantage of flaws in network protocols.
This article will explain what address poisoning attacks are, their types and consequences, and how to protect oneself against such attacks.
Address poisoning attacks in crypto, explained
In the world of cryptocurrencies, hostile actions where attackers influence or deceive consumers by tampering with cryptocurrency addresses are referred to as address poisoning attacks.
On a blockchain network, these addresses, which are made up of distinct alphanumeric strings, serve as the source or destination of transactions. These attacks use a variety of methods to undermine the integrity and security of cryptographic wallets and transactions.
Address poisoning attacks in the crypto space are mostly used to either illegally acquire digital assets or impair the smooth operation of blockchain networks. These attacks may encompass:
Theft
Attackers may trick users into transmitting their funds to malicious addresses using strategies such as phishing, transaction interception or address manipulation.
Disruption
Address poisoning can be used to disrupt the normal operations of blockchain networks by introducing congestion, delays or interruptions in transactions and smart contracts, reducing the effectiveness of the network.
Deception
Attackers frequently attempt to mislead cryptocurrency users by posing as well-known figures. This undermines community trust in the network and might result in erroneous transactions or confusion among users.
To protect digital assets and the general integrity of blockchain technology, address poisoning attacks highlight the significance of strict security procedures and constant attention within the cryptocurrency ecosystem.
Related: How to mitigate the security risks associated with crypto payments
Types of address poisoning attacks
Address poisoning attacks in crypto include phishing, transaction interception, address reuse exploitation, Sybil attacks, fake QR codes, address spoofing and smart contract vulnerabilities, each posing unique risks to users’ assets and network integrity.

Phishing attacks
In the cryptocurrency realm, phishing attacks are a prevalent type of address poisoning, which involves criminal actors building phony websites, emails or communications that closely resemble reputable companies like cryptocurrency exchanges or wallet providers.
These fraudulent platforms try to trick unsuspecting users into disclosing their login information, private keys or mnemonic phrases (recovery/seed phrases). Once gained, attackers can carry out unlawful transactions and get unauthorized access to victims’ Bitcoin (BTC) assets, for example.
For instance, hackers might build a fake exchange website that looks exactly like the real thing and ask consumers to log in. Once they do so, the attackers can gain access to customer funds on the actual exchange, which would result in substantial financial losses.
Transaction interception
Another method of address poisoning is transaction interception, in which attackers intercept valid cryptocurrency transactions and change the destination address. Funds destined for the genuine receiver are diverted by changing the recipient address to one under the attacker’s control. This kind of attack frequently involves malware compromising a user’s device or network or both.
Address reuse exploitation
Attackers monitor the blockchain for instances of address repetition before using such occurrences to their advantage. Reusing addresses can be risky for security because it might reveal the address’s transaction history and vulnerabilities. These weaknesses are used by malicious actors to access user wallets and steal funds.
For instance, if a user consistently gets funds from the same Ethereum address, an attacker might notice this pattern and take advantage of a flaw in the user’s wallet software to access the user’s funds without authorization.
Sybil attacks
To exert disproportionate control over a cryptocurrency network’s functioning, Sybil attacks entail the creation of several false identities or nodes. With this control, attackers are able to modify data, trick users, and maybe jeopardize the security of the network.
Attackers may use a large number of fraudulent nodes in the context of proof-of-stake (PoS) blockchain networks to significantly affect the consensus mechanism, giving them the ability to modify transactions and potentially double-spend cryptocurrencies.
Fake QR codes or payment addresses
Address poisoning can also happen when fake payment addresses or QR codes are distributed. Attackers often deliver these bogus codes in physical form to unwary users in an effort to trick them into sending cryptocurrency to a location they did not plan.
For example, a hacker might disseminate QR codes for cryptocurrency wallets that look real but actually include minor changes to the encoded address. Users who scan these codes unintentionally send money to the attacker’s address rather than that of the intended receiver, which causes financial losses.
Address spoofing
Attackers who use address spoofing create cryptocurrency addresses that closely resemble real ones. The idea is to trick users into transferring money to the attacker’s address rather than the one belonging to the intended recipient. The visual resemblance between the fake address and the real one is used in this method of address poisoning.
An attacker might, for instance, create a Bitcoin address that closely mimics the donation address of a reputable charity. Unaware donors may unintentionally transfer money to the attacker’s address while sending donations to the organization, diverting the funds from their intended use.
Smart contract vulnerabilities
Attackers take advantage of flaws or vulnerabilities in decentralized applications (DApps) or smart contracts on blockchain systems to carry out address poisoning. Attackers can reroute money or cause the contract to behave inadvertently by fiddling with how transactions are carried out. Users may suffer money losses as a result, and decentralized finance (DeFi) services may experience disruptions.
Consequences of address poisoning attacks
Address poisoning attacks can have devastating effects on both individual users and the stability of blockchain networks. Because attackers may steal crypto holdings or alter transactions to reroute money to their own wallets, these assaults frequently cause large financial losses for their victims.
Beyond monetary losses, these attacks may also result in a decline in confidence among cryptocurrency users. Users’ trust in the security and dependability of blockchain networks and related services may be damaged if they fall for fraudulent schemes or have their valuables stolen.
Additionally, some address poisoning assaults, such as Sybil attacks or the abuse of smart contract flaws, can prevent blockchain networks from operating normally, leading to delays, congestion or unforeseen consequences that have an effect on the entire ecosystem. These effects highlight the need for strong security controls and user awareness in the crypto ecosystem to reduce the risks of address poisoning attacks.
Related: How to put words into a Bitcoin address? Here’s how vanity addresses work
How to avoid address poisoning attacks
To protect users’ digital assets and keep blockchain networks secure, it is crucial to avoid address poisoning assaults in the cryptocurrency world. The following ways may help prevent being a target of such attacks:
Use fresh addresses
By creating a fresh crypto wallet address for each transaction, the chance of attackers connecting an address to a person’s identity or past transactions can be decreased. For instance, address poisoning attacks can be reduced by using hierarchical deterministic (HD) wallets, which create new addresses for each transaction and lessen the predictability of addresses.
Utilizing an HD wallet increases a user’s protection against address poisoning attacks because the wallet’s automatic address rotation makes it more difficult for hackers to redirect funds.
Utilize hardware wallets
When compared to software wallets, hardware wallets are a more secure alternative. They minimize exposure by keeping private keys offline.
Exercise caution when disclosing public addresses
People should exercise caution when disclosing their crypto addresses in the public sphere, especially on social media sites, and should opt for using pseudonyms.
Choose reputable wallets
It is important to use well-known wallet providers that are known for their security features and regular software updates to protect oneself from address poisoning and other attacks.
Regular updates
To stay protected against address poisoning attacks, it is essential to update the wallet software consistently with the newest security fixes.
Implement whitelisting
Use whitelisting to limit transactions to reputable sources. Some wallets or services allow users to whitelist particular addresses that can send funds to their wallets.
Consider multisig wallets
Wallets that require multiple private keys to approve a transaction are known as multisignature (multisig) wallets. These wallets can provide an additional degree of protection by requiring multiple signatures to approve a transaction.
Utilize blockchain analysis tools
To spot potentially harmful conduct, people can track and examine incoming transactions using blockchain analysis tools. Sending seemingly trivial, small quantities of crypto (dust) to numerous addresses is a common practice known as dusting. Analysts can spot potential poisoning efforts by examining these dust trade patterns.
Unspent transaction outputs (UTXOs) with tiny amounts of cryptocurrency are frequently the consequence of dust transactions. Analysts can locate possibly poisoned addresses by locating UTXOs connected to dust transactions.
Report suspected attacks
Individuals should respond right away in the event of a suspected address poisoning attack by getting in touch with the company that provides their crypto wallet through the official support channels and detailing the occurrence.
Additionally, they can report the occurrence to the relevant law enforcement or regulatory authorities for further investigation and potential legal action if the attack involved considerable financial harm or malevolent intent. To reduce possible risks and safeguard both individual and group interests in the cryptocurrency ecosystem, timely reporting is essential.
cryptocurrency bitcoin ethereum blockchain crypto btc cryptoUncategorized
February Employment Situation
By Paul Gomme and Peter Rupert The establishment data from the BLS showed a 275,000 increase in payroll employment for February, outpacing the 230,000…
By Paul Gomme and Peter Rupert
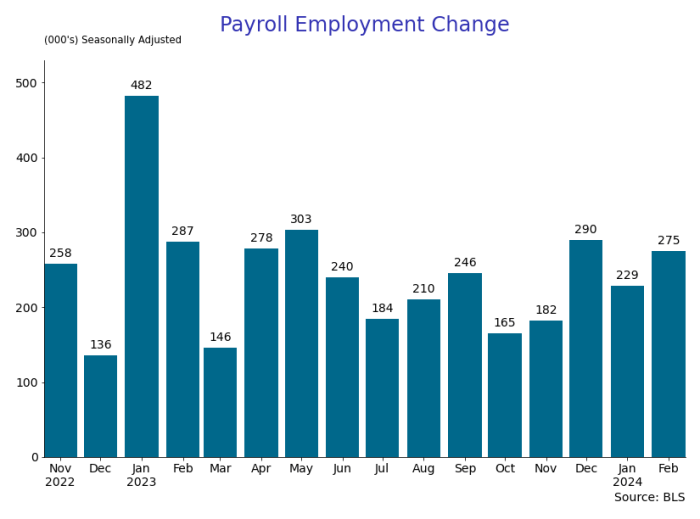
The establishment data from the BLS showed a 275,000 increase in payroll employment for February, outpacing the 230,000 average over the previous 12 months. The payroll data for January and December were revised down by a total of 167,000. The private sector added 223,000 new jobs, the largest gain since May of last year.

Temporary help services employment continues a steep decline after a sharp post-pandemic rise.


Average hours of work increased from 34.2 to 34.3. The increase, along with the 223,000 private employment increase led to a hefty increase in total hours of 5.6% at an annualized rate, also the largest increase since May of last year.

The establishment report, once again, beat “expectations;” the WSJ survey of economists was 198,000. Other than the downward revisions, mentioned above, another bit of negative news was a smallish increase in wage growth, from $34.52 to $34.57.

The household survey shows that the labor force increased 150,000, a drop in employment of 184,000 and an increase in the number of unemployed persons of 334,000. The labor force participation rate held steady at 62.5, the employment to population ratio decreased from 60.2 to 60.1 and the unemployment rate increased from 3.66 to 3.86. Remember that the unemployment rate is the number of unemployed relative to the labor force (the number employed plus the number unemployed). Consequently, the unemployment rate can go up if the number of unemployed rises holding fixed the labor force, or if the labor force shrinks holding the number unemployed unchanged. An increase in the unemployment rate is not necessarily a bad thing: it may reflect a strong labor market drawing “marginally attached” individuals from outside the labor force. Indeed, there was a 96,000 decline in those workers.


Earlier in the week, the BLS announced JOLTS (Job Openings and Labor Turnover Survey) data for January. There isn’t much to report here as the job openings changed little at 8.9 million, the number of hires and total separations were little changed at 5.7 million and 5.3 million, respectively.

As has been the case for the last couple of years, the number of job openings remains higher than the number of unemployed persons.

Also earlier in the week the BLS announced that productivity increased 3.2% in the 4th quarter with output rising 3.5% and hours of work rising 0.3%.

The bottom line is that the labor market continues its surprisingly (to some) strong performance, once again proving stronger than many had expected. This strength makes it difficult to justify any interest rate cuts soon, particularly given the recent inflation spike.
unemployment pandemic unemploymentUncategorized
Mortgage rates fall as labor market normalizes
Jobless claims show an expanding economy. We will only be in a recession once jobless claims exceed 323,000 on a four-week moving average.
Everyone was waiting to see if this week’s jobs report would send mortgage rates higher, which is what happened last month. Instead, the 10-year yield had a muted response after the headline number beat estimates, but we have negative job revisions from previous months. The Federal Reserve’s fear of wage growth spiraling out of control hasn’t materialized for over two years now and the unemployment rate ticked up to 3.9%. For now, we can say the labor market isn’t tight anymore, but it’s also not breaking.
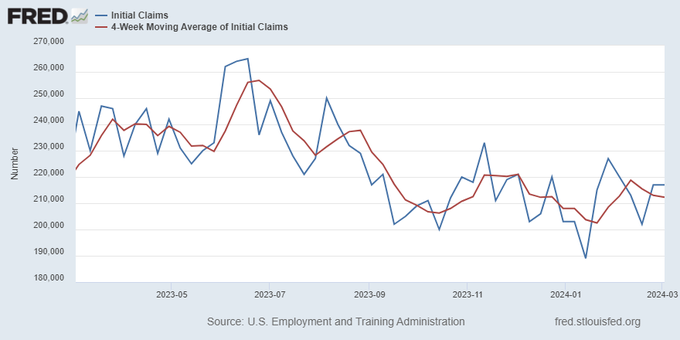
The key labor data line in this expansion is the weekly jobless claims report. Jobless claims show an expanding economy that has not lost jobs yet. We will only be in a recession once jobless claims exceed 323,000 on a four-week moving average.
From the Fed: In the week ended March 2, initial claims for unemployment insurance benefits were flat, at 217,000. The four-week moving average declined slightly by 750, to 212,250
Below is an explanation of how we got here with the labor market, which all started during COVID-19.
1. I wrote the COVID-19 recovery model on April 7, 2020, and retired it on Dec. 9, 2020. By that time, the upfront recovery phase was done, and I needed to model out when we would get the jobs lost back.
2. Early in the labor market recovery, when we saw weaker job reports, I doubled and tripled down on my assertion that job openings would get to 10 million in this recovery. Job openings rose as high as to 12 million and are currently over 9 million. Even with the massive miss on a job report in May 2021, I didn’t waver.
Currently, the jobs openings, quit percentage and hires data are below pre-COVID-19 levels, which means the labor market isn’t as tight as it once was, and this is why the employment cost index has been slowing data to move along the quits percentage.

3. I wrote that we should get back all the jobs lost to COVID-19 by September of 2022. At the time this would be a speedy labor market recovery, and it happened on schedule, too
Total employment data
4. This is the key one for right now: If COVID-19 hadn’t happened, we would have between 157 million and 159 million jobs today, which would have been in line with the job growth rate in February 2020. Today, we are at 157,808,000. This is important because job growth should be cooling down now. We are more in line with where the labor market should be when averaging 140K-165K monthly. So for now, the fact that we aren’t trending between 140K-165K means we still have a bit more recovery kick left before we get down to those levels.

From BLS: Total nonfarm payroll employment rose by 275,000 in February, and the unemployment rate increased to 3.9 percent, the U.S. Bureau of Labor Statistics reported today. Job gains occurred in health care, in government, in food services and drinking places, in social assistance, and in transportation and warehousing.
Here are the jobs that were created and lost in the previous month:

In this jobs report, the unemployment rate for education levels looks like this:
- Less than a high school diploma: 6.1%
- High school graduate and no college: 4.2%
- Some college or associate degree: 3.1%
- Bachelor’s degree or higher: 2.2%

Today’s report has continued the trend of the labor data beating my expectations, only because I am looking for the jobs data to slow down to a level of 140K-165K, which hasn’t happened yet. I wouldn’t categorize the labor market as being tight anymore because of the quits ratio and the hires data in the job openings report. This also shows itself in the employment cost index as well. These are key data lines for the Fed and the reason we are going to see three rate cuts this year.
recession unemployment covid-19 fed federal reserve mortgage rates recession recovery unemploymentUncategorized
Inside The Most Ridiculous Jobs Report In History: Record 1.2 Million Immigrant Jobs Added In One Month
Inside The Most Ridiculous Jobs Report In History: Record 1.2 Million Immigrant Jobs Added In One Month
Last month we though that the January…
Last month we though that the January jobs report was the "most ridiculous in recent history" but, boy, were we wrong because this morning the Biden department of goalseeked propaganda (aka BLS) published the February jobs report, and holy crap was that something else. Even Goebbels would blush.
What happened? Let's take a closer look.
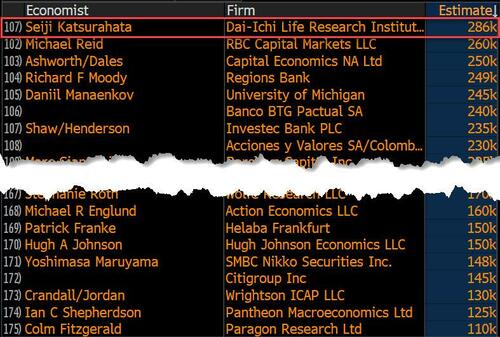
On the surface, it was (almost) another blockbuster jobs report, certainly one which nobody expected, or rather just one bank out of 76 expected. Starting at the top, the BLS reported that in February the US unexpectedly added 275K jobs, with just one research analyst (from Dai-Ichi Research) expecting a higher number.
Some context: after last month's record 4-sigma beat, today's print was "only" 3 sigma higher than estimates. Needless to say, two multiple sigma beats in a row used to only happen in the USSR... and now in the US, apparently.
Before we go any further, a quick note on what last month we said was "the most ridiculous jobs report in recent history": it appears the BLS read our comments and decided to stop beclowing itself. It did that by slashing last month's ridiculous print by over a third, and revising what was originally reported as a massive 353K beat to just 229K, a 124K revision, which was the biggest one-month negative revision in two years!
Of course, that does not mean that this month's jobs print won't be revised lower: it will be, and not just that month but every other month until the November election because that's the only tool left in the Biden admin's box: pretend the economic and jobs are strong, then revise them sharply lower the next month, something we pointed out first last summer and which has not failed to disappoint once.
In the past month the Biden department of goalseeking stuff higher before revising it lower, has revised the following data sharply lower:
— zerohedge (@zerohedge) August 30, 2023
- Jobs
- JOLTS
- New Home sales
- Housing Starts and Permits
- Industrial Production
- PCE and core PCE
To be fair, not every aspect of the jobs report was stellar (after all, the BLS had to give it some vague credibility). Take the unemployment rate, after flatlining between 3.4% and 3.8% for two years - and thus denying expectations from Sahm's Rule that a recession may have already started - in February the unemployment rate unexpectedly jumped to 3.9%, the highest since February 2022 (with Black unemployment spiking by 0.3% to 5.6%, an indicator which the Biden admin will quickly slam as widespread economic racism or something).
And then there were average hourly earnings, which after surging 0.6% MoM in January (since revised to 0.5%) and spooking markets that wage growth is so hot, the Fed will have no choice but to delay cuts, in February the number tumbled to just 0.1%, the lowest in two years...
... for one simple reason: last month's average wage surge had nothing to do with actual wages, and everything to do with the BLS estimate of hours worked (which is the denominator in the average wage calculation) which last month tumbled to just 34.1 (we were led to believe) the lowest since the covid pandemic...
... but has since been revised higher while the February print rose even more, to 34.3, hence why the latest average wage data was once again a product not of wages going up, but of how long Americans worked in any weekly period, in this case higher from 34.1 to 34.3, an increase which has a major impact on the average calculation.
While the above data points were examples of some latent weakness in the latest report, perhaps meant to give it a sheen of veracity, it was everything else in the report that was a problem starting with the BLS's latest choice of seasonal adjustments (after last month's wholesale revision), which have gone from merely laughable to full clownshow, as the following comparison between the monthly change in BLS and ADP payrolls shows. The trend is clear: the Biden admin numbers are now clearly rising even as the impartial ADP (which directly logs employment numbers at the company level and is far more accurate), shows an accelerating slowdown.
But it's more than just the Biden admin hanging its "success" on seasonal adjustments: when one digs deeper inside the jobs report, all sorts of ugly things emerge... such as the growing unprecedented divergence between the Establishment (payrolls) survey and much more accurate Household (actual employment) survey. To wit, while in January the BLS claims 275K payrolls were added, the Household survey found that the number of actually employed workers dropped for the third straight month (and 4 in the past 5), this time by 184K (from 161.152K to 160.968K).
This means that while the Payrolls series hits new all time highs every month since December 2020 (when according to the BLS the US had its last month of payrolls losses), the level of Employment has not budged in the past year. Worse, as shown in the chart below, such a gaping divergence has opened between the two series in the past 4 years, that the number of Employed workers would need to soar by 9 million (!) to catch up to what Payrolls claims is the employment situation.
There's more: shifting from a quantitative to a qualitative assessment, reveals just how ugly the composition of "new jobs" has been. Consider this: the BLS reports that in February 2024, the US had 132.9 million full-time jobs and 27.9 million part-time jobs. Well, that's great... until you look back one year and find that in February 2023 the US had 133.2 million full-time jobs, or more than it does one year later! And yes, all the job growth since then has been in part-time jobs, which have increased by 921K since February 2023 (from 27.020 million to 27.941 million).
Here is a summary of the labor composition in the past year: all the new jobs have been part-time jobs!
But wait there's even more, because now that the primary season is over and we enter the heart of election season and political talking points will be thrown around left and right, especially in the context of the immigration crisis created intentionally by the Biden administration which is hoping to import millions of new Democratic voters (maybe the US can hold the presidential election in Honduras or Guatemala, after all it is their citizens that will be illegally casting the key votes in November), what we find is that in February, the number of native-born workers tumbled again, sliding by a massive 560K to just 129.807 million. Add to this the December data, and we get a near-record 2.4 million plunge in native-born workers in just the past 3 months (only the covid crash was worse)!
The offset? A record 1.2 million foreign-born (read immigrants, both legal and illegal but mostly illegal) workers added in February!
Said otherwise, not only has all job creation in the past 6 years has been exclusively for foreign-born workers...

... but there has been zero job-creation for native born workers since June 2018!
This is a huge issue - especially at a time of an illegal alien flood at the southwest border...
... and is about to become a huge political scandal, because once the inevitable recession finally hits, there will be millions of furious unemployed Americans demanding a more accurate explanation for what happened - i.e., the illegal immigration floodgates that were opened by the Biden admin.
Which is also why Biden's handlers will do everything in their power to insure there is no official recession before November... and why after the election is over, all economic hell will finally break loose. Until then, however, expect the jobs numbers to get even more ridiculous.
-

 Uncategorized2 weeks ago
Uncategorized2 weeks agoAll Of The Elements Are In Place For An Economic Crisis Of Staggering Proportions
-

 Uncategorized1 month ago
Uncategorized1 month agoCathie Wood sells a major tech stock (again)
-

 Uncategorized3 weeks ago
Uncategorized3 weeks agoCalifornia Counties Could Be Forced To Pay $300 Million To Cover COVID-Era Program
-

 Uncategorized2 weeks ago
Uncategorized2 weeks agoApparel Retailer Express Moving Toward Bankruptcy
-

 Uncategorized3 weeks ago
Uncategorized3 weeks agoIndustrial Production Decreased 0.1% in January
-

 International1 day ago
International1 day agoWalmart launches clever answer to Target’s new membership program
-

 Uncategorized3 weeks ago
Uncategorized3 weeks agoRFK Jr: The Wuhan Cover-Up & The Rise Of The Biowarfare-Industrial Complex
-

 Uncategorized3 weeks ago
Uncategorized3 weeks agoGOP Efforts To Shore Up Election Security In Swing States Face Challenges




































