Government
Chesapeake Files For Bankruptcy, Wiping Out $7 Billion In Debt And Any Existing Equity Value
Chesapeake Files For Bankruptcy, Wiping Out $7 Billion In Debt And Any Existing Equity Value
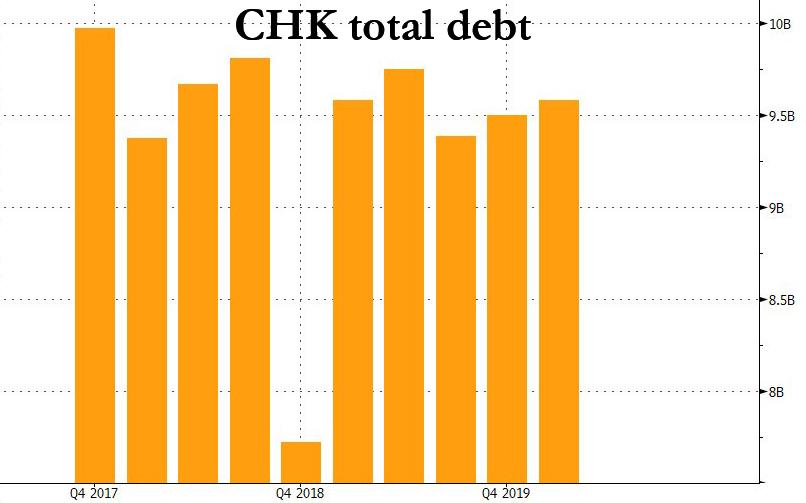
After years of melting, the Chesapeake icecube is finally history: at exactly 350pm on Sunday afternoon, the company that many say launched the US shale boom, finally gave up and filed for a pre-packaged bankruptcy in the Southern District of Texas. In so doing, the company with roughly $10 billion in debt has become one of the biggest victims of a spectacular collapse in energy demand from the virus-induced global recession, and follows the collapse of another high-flyer in the US oil patch, Whiting Petroleum, which filed for Chapter 11 at the start of April after championing what was once the premiere U.S. shale field, the Bakken of North Dakota.
As part of its prepack agreement, Chesapeake announced that it had entered into a Restructuring Support Agreement ("RSA") with 100% of the lenders under its revolving credit facility, holders of approximately 87% of the obligations under its Term Loan Agreement, approximately 60% of its senior secured second lien notes due 2025, and approximately 27% of its senior unsecured notes, pursuant to which Chesapeake will implement a Chapter 11 plan of reorganization to eliminate approximately $7 billion of debt.
Of course, since 73% of unsecured bondholders refused to sign off on the deal, expect a very vicious bankruptcy fight over the recoveries, as hedge funds that accumulated positions in the bonds unleash hell in their fight with the secureds (even as the equity committee claims that all classes above it should be unimpaired).
Also, we have some bad news for Jefferies, which won't be able to repeat its hilarious attempt to fund the company in bankruptcy by selling stock to Robnhood daytraders: as part of the RSA, the Company has secured $925 million in debtor-in-possession financing lenders under Chesapeake's revolving credit facility. The DIP will provide Chesapeake the capital necessary to fund its operations during the Court-supervised Chapter 11 reorganization proceedings.
To summarize: Chesapeake which enters bankruptcy with just over $9.5 billion in debt...
... will eliminate about $7 billion of it, and emerge with a $2.5 billion exit financing, consisting of a new $1.75 billion revolving credit facility and a new $750 million term loan. Additionally, according to the RSA, the Company has the support of its term loan lenders and secured note holders to backstop a $600 million rights offering upon exit.
Doug Lawler, Chesapeake's President and Chief Executive Officer, stated, "We are fundamentally resetting Chesapeake's capital structure and business to address our legacy financial weaknesses and capitalize on our substantial operational strengths. By eliminating approximately $7 billion of debt and addressing the legacy contractual obligations that have hindered our performance, we are positioning Chesapeake to capitalize on our diverse operating platform and proven track record of improving capital and operating efficiencies and technical excellence. With these demonstrated strengths, and the benefit of an appropriately sized capital structure, Chesapeake will be uniquely positioned to emerge from the Chapter 11 process as a stronger and more competitive enterprise."
Lawler concluded, "Over the last several years, our dedicated employees have transformed Chesapeake's business — improving capital efficiency and operational performance, eliminating costs, reducing debt and diversifying our portfolio. Despite having removed over $20 billion of leverage and financial commitments, we believe this restructuring is necessary for the long-term success and value creation of the business."
In addition to leverage, Lawler also removed all the equity value, because with $7 billion in senior debt destroyed, there is no question here: the common stock has no value and will almost certainly be delisted immediately to avoid any potential "misunderstandings" should an army of 10-year-old veteran Robinhood traders decided to ramp it up by a few hundred percent.
And speaking of the company's stock and daytrading activity, it is as if 216,915 Robinhood traders suddenly cried out in terror and were suddenly silenced.
Why? Because according to RobinTrack, some 216,915 users who held on to the stock as of April 14, and whose number has certainly surged in recent days after the stock soared as high as $84.75 on June 8 during the peak of the retail euphoria boom that sent bankrupt Hertz stock also soaring and inspired Jefferies to read this blog and come up with the now-failed attempt to sell worthless stock to Robinhooders.
That said, in a market as insanely broken as this one, it is certainly possible that CHK stock which the company admits is worth about a negative $7 billion, could surge tomorrow... just because.
* * *
Finally, some corporate history courtesy of Bloomberg:
About a decade ago, Chesapeake was a $37.5 billion giant led by the late Aubrey McClendon, a colorful and outspoken advocate for the natural gas industry, who died on March 2, 2016 in what appeared to be a suicide. It was at the forefront of the fracking revolution that transformed the U.S. oil and gas industry by setting off a scramble for previously untapped shale reserves. The company cut eye-popping checks to Fort Worth businesses and residents as inducements to drill on their land in the Barnett Shale of North Texas, America’s first shale field to hit the big time.
Those heady days didn’t last. U.S. natural gas slumped after the financial crisis as the frackers overwhelmed demand, and prices still haven’t revisited their previous highs. Investors soured on Chesapeake, which by that point wasn’t only debt-laden but saddled with a real estate empire that included shopping centers, a church, and a grocery store. McClendon was ousted in 2013 and was killed in an auto accident three years later.
In subsequent years, management sought to compensate for the decline in its gas fortunes by shifting into oil exploration as fracking turned the U.S. into the world’s largest producer of crude as well as a major exporter. However, any optimism about that strategy evaporated with oil’s recent price collapse amid the Covid-19 pandemic.
International
Shakira’s net worth
After 12 albums, a tax evasion case, and now a towering bronze idol sculpted in her image, how much is Shakira worth more than 4 decades into her care…

Shakira’s considerable net worth is no surprise, given her massive popularity in Latin America, the U.S., and elsewhere.
In fact, the belly-dancing contralto queen is the second-wealthiest Latin-America-born pop singer of all time after Gloria Estefan. (Interestingly, Estefan actually helped a young Shakira translate her breakout album “Laundry Service” into English, hugely propelling her stateside success.)
Since releasing her first record at age 13, Shakira has spent decades recording albums in both Spanish and English and performing all over the world. Over the course of her 40+ year career, she helped thrust Latin pop music into the American mainstream, paving the way for the subsequent success of massively popular modern acts like Karol G and Bad Bunny.
In December 2023, a 21-foot-tall beachside bronze statue of the “Hips Don’t Lie” singer was unveiled in her Colombian hometown of Barranquilla, making her a permanent fixture in the city’s skyline and cementing her legacy as one of Latin America’s most influential entertainers.
After 12 albums, a plethora of film and television appearances, a highly publicized tax evasion case, and now a towering bronze idol sculpted in her image, how much is Shakira worth? What does her income look like? And how does she spend her money?
How much is Shakira worth?
In late 2023, Spanish sports and lifestyle publication Marca reported Shakira’s net worth at $400 million, citing Forbes as the figure’s source (although Forbes’ profile page for Shakira does not list a net worth — and didn’t when that article was published).
Most other sources list the singer’s wealth at an estimated $300 million, and almost all of these point to Celebrity Net Worth — a popular but dubious celebrity wealth estimation site — as the source for the figure.
A $300 million net worth would make Shakira the third-richest Latina pop star after Gloria Estefan ($500 million) and Jennifer Lopez ($400 million), and the second-richest Latin-America-born pop singer after Estefan (JLo is Puerto Rican but was born in New York).
Shakira’s income: How much does she make annually?
Entertainers like Shakira don’t have predictable paychecks like ordinary salaried professionals. Instead, annual take-home earnings vary quite a bit depending on each year’s album sales, royalties, film and television appearances, streaming revenue, and other sources of income. As one might expect, Shakira’s earnings have fluctuated quite a bit over the years.
From June 2018 to June 2019, for instance, Shakira was the 10th highest-earning female musician, grossing $35 million, according to Forbes. This wasn’t her first time gracing the top 10, though — back in 2012, she also landed the #10 spot, bringing in $20 million, according to Billboard.
In 2023, Billboard listed Shakira as the 16th-highest-grossing Latin artist of all time.

How much does Shakira make from her concerts and tours?
A large part of Shakira’s wealth comes from her world tours, during which she sometimes sells out massive stadiums and arenas full of passionate fans eager to see her dance and sing live.
According to a 2020 report by Pollstar, she sold over 2.7 million tickets across 190 shows that grossed over $189 million between 2000 and 2020. This landed her the 19th spot on a list of female musicians ranked by touring revenue during that period. In 2023, Billboard reported a more modest touring revenue figure of $108.1 million across 120 shows.
In 2003, Shakira reportedly generated over $4 million from a single show on Valentine’s Day at Foro Sol in Mexico City. 15 years later, in 2018, Shakira grossed around $76.5 million from her El Dorado World Tour, according to Touring Data.
Related: RuPaul's net worth: Everything to know about the cultural icon and force behind 'Drag Race'
How much has Shakira made from her album sales?
According to a 2023 profile in Variety, Shakira has sold over 100 million records throughout her career. “Laundry Service,” the pop icon’s fifth studio album, was her most successful, selling over 13 million copies worldwide, according to TheRichest.
Exactly how much money Shakira has taken home from her album sales is unclear, but in 2008, it was widely reported that she signed a 10-year contract with LiveNation to the tune of between $70 and $100 million to release her subsequent albums and manage her tours.

How much did Shakira make from her Super Bowl and World Cup performances?
Shakira co-wrote one of her biggest hits, “Waka Waka (This Time for Africa),” after FIFA selected her to create the official anthem for the 2010 World Cup in South Africa. She performed the song, along with several of her existing fan-favorite tracks, during the event’s opening ceremonies. TheThings reported in 2023 that the song generated $1.4 million in revenue, citing Popnable for the figure.
A decade later, 2020’s Superbowl halftime show featured Shakira and Jennifer Lopez as co-headliners with guest performances by Bad Bunny and J Balvin. The 14-minute performance was widely praised as a high-energy celebration of Latin music and dance, but as is typical for Super Bowl shows, neither Shakira nor JLo was compensated beyond expenses and production costs.
The exposure value that comes with performing in the Super Bowl Halftime Show, though, is significant. It is typically the most-watched television event in the U.S. each year, and in 2020, a 30-second Super Bowl ad spot cost between $5 and $6 million.
How much did Shakira make as a coach on “The Voice?”
Shakira served as a team coach on the popular singing competition program “The Voice” during the show’s fourth and sixth seasons. On the show, celebrity musicians coach up-and-coming amateurs in a team-based competition that eventually results in a single winner. In 2012, The Hollywood Reporter wrote that Shakira’s salary as a coach on “The Voice” was $12 million.
Related: John Cena's net worth: The wrestler-turned-actor's investments, businesses, and more
How does Shakira spend her money?
Shakira doesn’t just make a lot of money — she spends it, too. Like many wealthy entertainers, she’s purchased her share of luxuries, but Barranquilla’s barefoot belly dancer is also a prolific philanthropist, having donated tens of millions to charitable causes throughout her career.
Private island
Back in 2006, she teamed up with Roger Waters of Pink Floyd fame and Spanish singer Alejandro Sanz to purchase Bonds Cay, a 550-acre island in the Bahamas, which was listed for $16 million at the time.
Along with her two partners in the purchase, Shakira planned to develop the island to feature housing, hotels, and an artists’ retreat designed to host a revolving cast of artists-in-residence. This plan didn’t come to fruition, though, and as of this article’s last update, the island was once again for sale on Vladi Private Islands.
Real estate and vehicles
Like most wealthy celebs, Shakira’s portfolio of high-end playthings also features an array of luxury properties and vehicles, including a home in Barcelona, a villa in Cyprus, a Miami mansion, and a rotating cast of Mercedes-Benz vehicles.
Philanthropy and charity
Shakira doesn’t just spend her massive wealth on herself; the “Queen of Latin Music” is also a dedicated philanthropist and regularly donates portions of her earnings to the Fundación Pies Descalzos, or “Barefoot Foundation,” a charity she founded in 1997 to “improve the education and social development of children in Colombia, which has suffered decades of conflict.” The foundation focuses on providing meals for children and building and improving educational infrastructure in Shakira’s hometown of Barranquilla as well as four other Colombian communities.
In addition to her efforts with the Fundación Pies Descalzos, Shakira has made a number of other notable donations over the years. In 2007, she diverted a whopping $40 million of her wealth to help rebuild community infrastructure in Peru and Nicaragua in the wake of a devastating 8.0 magnitude earthquake. Later, during the COVID-19 pandemic in 2020, Shakira donated a large supply of N95 masks for healthcare workers and ventilators for hospital patients to her hometown of Barranquilla.
Back in 2010, the UN honored Shakira with a medal to recognize her dedication to social justice, at which time the Director General of the International Labour Organization described her as a “true ambassador for children and young people.”

Shakira’s tax fraud scandal: How much did she pay?
In 2018, prosecutors in Spain initiated a tax evasion case against Shakira, alleging she lived primarily in Spain from 2012 to 2014 and therefore failed to pay around $14.4 million in taxes to the Spanish government. Spanish law requires anyone who is “domiciled” (i.e., living primarily) in Spain for more than half of the year to pay income taxes.
During the period in question, Shakira listed the Bahamas as her primary residence but did spend some time in Spain, as she was dating Gerard Piqué, a professional footballer and Spanish citizen. The couple’s first son, Milan, was also born in Barcelona during this period.
Shakira maintained that she spent far fewer than 183 days per year in Spain during each of the years in question. In an interview with Elle Magazine, the pop star opined that “Spanish tax authorities saw that I was dating a Spanish citizen and started to salivate. It's clear they wanted to go after that money no matter what."
Prosecutors in the case sought a fine of almost $26 million and a possible eight-year prison stint, but in November of 2023, Shakira took a deal to close the case, accepting a fine of around $8 million and a three-year suspended sentence to avoid going to trial. In reference to her decision to take the deal, Shakira stated, "While I was determined to defend my innocence in a trial that my lawyers were confident would have ruled in my favour [had the trial proceeded], I have made the decision to finally resolve this matter with the best interest of my kids at heart who do not want to see their mom sacrifice her personal well-being in this fight."
How much did the Shakira statue in Barranquilla cost?
In late 2023, a 21-foot-tall bronze likeness of Shakira was unveiled on a waterfront promenade in Barranquilla. The city’s then-mayor, Jaime Pumarejo, commissioned Colombian sculptor Yino Márquez to create the statue of the city’s treasured pop icon, along with a sculpture of the city’s coat of arms.
According to the New York Times, the two sculptures cost the city the equivalent of around $180,000. A plaque at the statue’s base reads, “A heart that composes, hips that don’t lie, an unmatched talent, a voice that moves the masses and bare feet that march for the good of children and humanity.”
Related: Taylor Swift net worth: The most successful entertainer joins the billionaire's club
bonds pandemic covid-19 real estate africa mexico spainInternational
Delta Air Lines adds a new route travelers have been asking for
The new Delta seasonal flight to the popular destination will run daily on a Boeing 767-300.

Those who have tried to book a flight from North America to Europe in the summer of 2023 know just how high travel demand to the continent has spiked.
At 2.93 billion, visitors to the countries making up the European Union had finally reached pre-pandemic levels last year while North Americans in particular were booking trips to both large metropolises such as Paris and Milan as well as smaller cities growing increasingly popular among tourists.
Related: A popular European city is introducing the highest 'tourist tax' yet
As a result, U.S.-based airlines have been re-evaluating their networks to add more direct routes to smaller European destinations that most travelers would have previously needed to reach by train or transfer flight with a local airline.
Shutterstock
Delta Air Lines: ‘Glad to offer customers increased choice…’
By the end of March, Delta Air Lines (DAL) will be restarting its route between New York’s JFK and Marco Polo International Airport in Venice as well as launching two new flights to Venice from Atlanta. One will start running this month while the other will be added during peak demand in the summer.
More Travel:
- A new travel term is taking over the internet (and reaching airlines and hotels)
- The 10 best airline stocks to buy now
- Airlines see a new kind of traveler at the front of the plane
“As one of the most beautiful cities in the world, Venice is hugely popular with U.S. travelers, and our flights bring valuable tourism and trade opportunities to the city and the region as well as unrivalled opportunities for Venetians looking to explore destinations across the Americas,” Delta’s SVP for Europe Matteo Curcio said in a statement. “We’re glad to offer customers increased choice this summer with flights from New York and additional service from Atlanta.”
The JFK-Venice flight will run on a Boeing 767-300 (BA) and have 216 seats including higher classes such as Delta One, Delta Premium Select and Delta Comfort Plus.
Delta offers these features on the new flight
Both the New York and Atlanta flights are seasonal routes that will be pulled out of service in October. Both will run daily while the first route will depart New York at 8:55 p.m. and arrive in Venice at 10:15 a.m. local time on the way there, while leaving Venice at 12:15 p.m. to arrive at JFK at 5:05 p.m. on the way back.
According to Delta, this will bring its service to 17 flights from different U.S. cities to Venice during the peak summer period. As with most Delta flights at this point, passengers in all fare classes will have access to free Wi-Fi during the flight.
Those flying in Delta’s highest class or with access through airline status or a credit card will also be able to use the new Delta lounge that is part of the airline’s $12 billion terminal renovation and is slated to open to travelers in the coming months. The space will take up more than 40,000 square feet and have an outdoor terrace.
“Delta One customers can stretch out in a lie-flat seat and enjoy premium amenities like plush bedding made from recycled plastic bottles, more beverage options, and a seasonal chef-curated four-course meal,” Delta said of the new route. “[…] All customers can enjoy a wide selection of in-flight entertainment options and stay connected with Wi-Fi and enjoy free mobile messaging.”
stocks pandemic european europeGovernment
Stock Market Today: Stocks turn lower as factory inflation spikes, retail sales miss target
Stocks will navigate the last major data releases prior to next week’s Fed rate meeting in Washington.

Check back for updates throughout the trading day
U.S. stocks edged lower Thursday following a trio of key economic releases that have added to the current inflation puzzle as investors shift focus to the Federal Reserve's March policy meeting next week in Washington.
Updated at 9:59 AM EDT
Red start
Stocks are now falling sharply following the PPI inflation data and retail sales miss, with the S&P 500 marked 18 points lower, or 0.36%, in the opening half hour of trading.
The Dow, meanwhile, was marked 92 points lower while the Nasdaq slipped 67 points.
Treasury yields are also on the move, with 2-year notes rising 5 basis points on the session to 4.679% and 10-year notes pegged 7 basis points higher at 4.271%.
The probability of a June rate cut has moved below 60% after the higher-than-expected CPI/PPI reports. A week ago this probability was 74% and a month ago it was 82%. pic.twitter.com/9W01oWU96G
— Charlie Bilello (@charliebilello) March 14, 2024
Updated at 9:44 AM EDT
Under Water
Under Armour (UAA) shares slumped firmly lower in early trading following the sportswear group's decision to bring back founder Kevin Plank as CEO, replacing the outgoing Stephanie Linnartz.
Plank, who founded Under Armour in 1996, left the group in May of 2021 just weeks before the group revealed that it was co-operating with investigations from both the Securities and Exchange Commission and the U.S. Department of Justice into the company's revenue recognition accounting.
Under Armour shares were marked 10.6% lower in early trading to change hands at $7.21 each.
Updated at 9:22 AM EDT
Steely resolve
U.S. Steel (X) shares extended their two-day decline Thursday, falling 5.75% in pre-market trading following multiple reports that suggest President Joe Biden will push to prevent Japan's Nippon Steel from buying the Pittsburgh-based group.
Both Reuters and the Associated Press have said Biden will express his views to Prime Minister Kishida Yuko ahead of a planned State Visit next month at the White House.
Related: US Steel soars on $15 billion Nippon Steel takeover; United Steelworkers slams deal
Updated at 8:52 AM EDT
Clear as mud
Retail sales rebounded last month, but the overall tally of $700.7 billion missed Street forecasts and suggests the recent uptick in inflation could be holding back discretionary spending.
A separate reading of factory inflation, meanwhile, showed prices spiking by 1.6%, on the year, and 0.6% on the month, amid a jump in goods prices.
U.S. stocks held earlier gains following the data release, with futures tied to the S&P 500 indicating an opening bell gain of 10 points, while the Dow was called 140 points higher. The Nasdaq, meanwhile, is looking at a more modest 40 point gain.
Benchmark 10-year Treasury note yields edged 3 basis points lower to 4.213% while two-year notes were little-changed at 4.626%.
The #PPI troughed 8 months ago, yet the economic consensus and even the #Fed believes #inflation has been conquered. Forget the forecasts for multiple rate cuts. pic.twitter.com/ZNIiKLWdFA
— Richard Bernstein Advisors (@RBAdvisors) March 14, 2024
Stock Market Today
Stocks finished lower last night, with the S&P 500 ending modestly in the red and the Nasdaq falling around 0.5%. The declines came amid an uptick in Treasury yields tied to concern that inflation pressures have failed to ease over the opening months of the year.
A better-than-expected auction of $22 billion in 30-year bonds, drawing the strongest overall demand since last June, steadied the overall market, but stocks still slipped into the close with an eye towards today's dataset.
The Commerce Department will publish its February reading of factory-gate inflation at 8:30 am Eastern Time. Analysts are expecting a slowdown in the key core reading, which feeds into the Fed's favored PCE price index.
Retail sales figures for the month are also set for an 8:30 am release as investors search for clues on consumer strength, tied to a resilient job market. Those factors could give the Fed more justification to wait until the summer months to begin the first of its three projected rate cuts.
"The case for a gradual but sustained slowdown in growth in consumers’ spending from 2023’s robust pace is persuasive," said Ian Shepherdson of Pantheon Macroeconomics.
"Most households have run down the excess savings accumulated during the pandemic, while the cost of credit has jumped and last year’s plunge in home sales has depressed demand housing-related retail items like furniture and appliances," he added.
Benchmark 10-year Treasury yields are holding steady at 4.196% heading into the start of the New York trading session, while 2-year notes were pegged at 4.628%.
With Fed officials in a quiet period, requiring no public comments ahead of next week's meeting in Washington, the U.S. dollar index is trading in a narrow range against its global peers and was last marked 0.06% higher at 102.852.
On Wall Street, futures tied to the S&P 500 are indicating an opening bell gain of around 19 points, with the Dow Jones Industrial Average indicating a 140-point advance.
The tech-focused Nasdaq, which is up 7.77% for the year, is priced for a gain of around 95 points, with Tesla (TSLA) once again sliding into the red after ending the Wednesday session at a 10-month low.
In Europe, the regionwide Stoxx 600 was marked 0.35% higher in early Frankfurt trading, while Britain's FTSE 100 slipped 0.09% in London.
Overnight in Asia, the Nikkei 225 gained 0.29% as investors looked to a key series of wage negotiation figures from key unions that are likely to see the biggest year-on-year pay increases in three decades.
The broader MSCI ex-Japan benchmark, meanwhile, rose 0.18% into the close of trading.
Related: Veteran fund manager picks favorite stocks for 2024
bonds pandemic dow jones sp 500 nasdaq ftse stocks rate cut fed federal reserve home sales white house japan europe-

 Uncategorized3 weeks ago
Uncategorized3 weeks agoAll Of The Elements Are In Place For An Economic Crisis Of Staggering Proportions
-

 International6 days ago
International6 days agoEyePoint poaches medical chief from Apellis; Sandoz CFO, longtime BioNTech exec to retire
-

 Uncategorized4 weeks ago
Uncategorized4 weeks agoCalifornia Counties Could Be Forced To Pay $300 Million To Cover COVID-Era Program
-

 Uncategorized3 weeks ago
Uncategorized3 weeks agoApparel Retailer Express Moving Toward Bankruptcy
-

 Uncategorized4 weeks ago
Uncategorized4 weeks agoIndustrial Production Decreased 0.1% in January
-

 International6 days ago
International6 days agoWalmart launches clever answer to Target’s new membership program
-

 Uncategorized4 weeks ago
Uncategorized4 weeks agoRFK Jr: The Wuhan Cover-Up & The Rise Of The Biowarfare-Industrial Complex
-

 Uncategorized3 weeks ago
Uncategorized3 weeks agoGOP Efforts To Shore Up Election Security In Swing States Face Challenges























